- The estimated number of mobile phones users around the globe in 2019 surpass five billion people.
- Cyber security professionals rank mobile devices as the hardest enterprise asset to defend
Mobile Device Security
Importance of mobile device security – In the today’s world, it is very unusual to find anyone who doesn’t own some kind of mobile device. Mobile phones or tablets are manufactured by numerous number of companies and there are many different service providers that equip the majority of world’s population with mobile devices.
It is estimated that the number of mobile phone users by 2019 will surpass five billion people around the globe. In addition to the social and economical effects of this massive increase, there is a definite increase in the number of cyber crimes. Cyber criminals have taken advantage of this massive growth and developed methods to take advantage of the increased number of possible targets.
There are many opportunities for cyber-criminals to access their targets: through apps, operating systems and software, and by identifying and taking advantages of defects in security before the programmers do and a patch a released.
Threats to Mobile Device Security
An outdated view of hacking, malware or viruses would limit this activity to desktop computers or laptops. The reality is that mobiles are just as at risk. In fact, reported incidents are in the range of 16 million attacks. A mobile device can be at risk from several different methods, some of which include:
Malicious, or Insecure Apps
Malicious or insecure apps contain cyber security flaws in data storage, communication, or authentication practices, meaning they contain at least one common security vulnerability that can be exploited.
Data Sniffing
Data sniffing by capturing, monitoring and scanning traffic moving across a network. Active sniffingwill monitor traffic and it can also alter it in some way to the like of the attacking party.
Fake WiFi Networks
Fake WiFi networks poses as a legitimate wireless service provider to intercept information that users transmit.
Vulnerabilities
Vulnerabilities within operating systems can be used to gain control of mobile devices, and depending on the operating system and its software, some mobile devices can be easily patched. However, others may be more difficult to patch, which could leave them vulnerable.
Inactive Apps
Inactive apps that are installed on mobile devices but unused and have unsecured access to personal and corporate information pose a significant danger to devices if they are not uninstalled properly.
In addition to the above threats, mobile devices are also susceptible to physical attacks due to their portability.
But all is not lost. Here are some practical steps that will help you minimize the exposure of your mobile device to digital and physical threats.
Mobile Device Security Tips
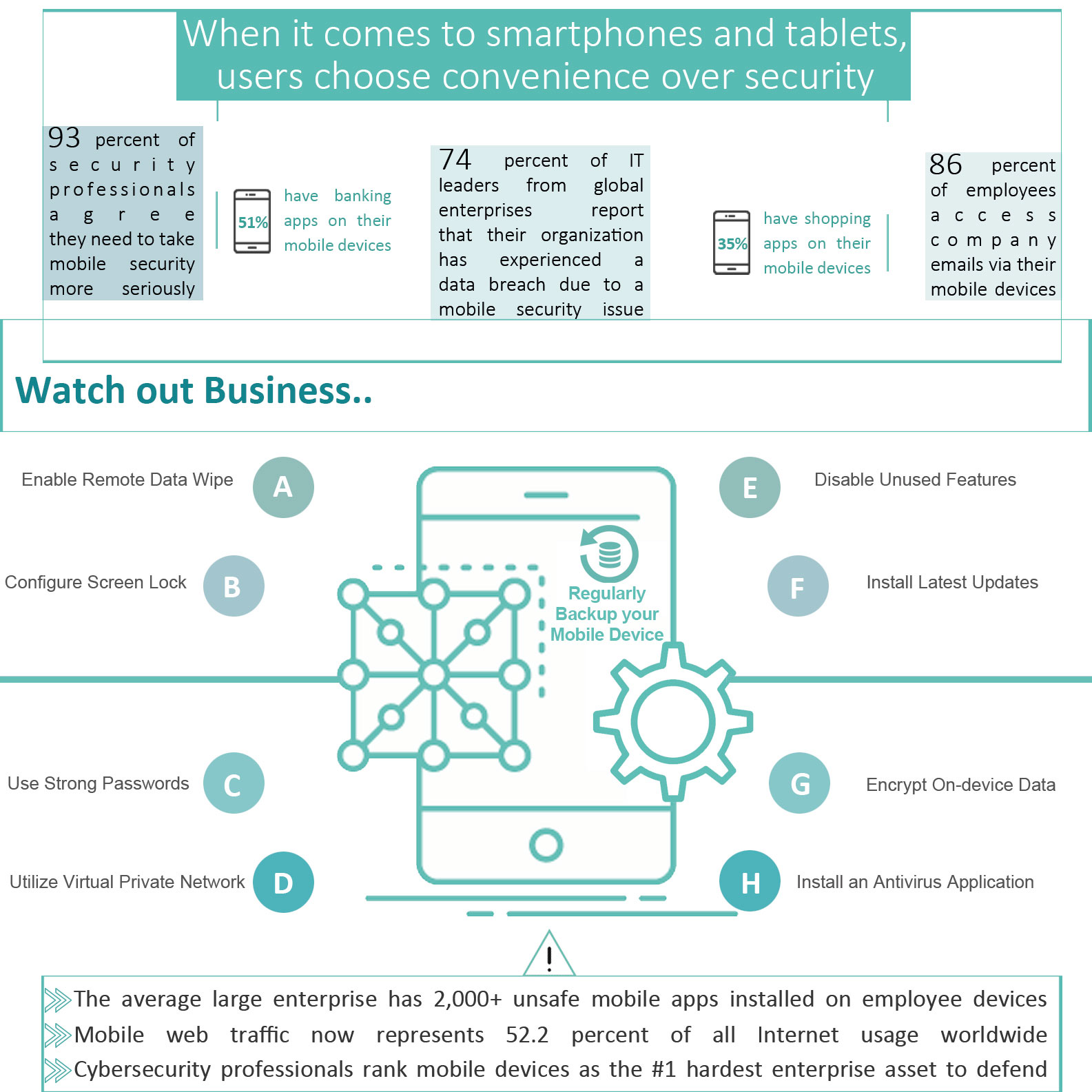
Use strong passwords and/or Bio-metrics
Passwords are always important, but even more so when you consider that the device could be stolen and in the possession of someone who has unlimited access and time to try various values.
Screen Lock
The display should be configured to time out after a short period of inactivity and the screen locked with a password.
Remote Wipe/Sanitation
Many programs, such as Find my iPhone or Google Play Protect, even Microsoft Exchange Server (if an exchange email is configured on mobile device) allow you to send a command to the mobile device that will remotely clear the data on that device.
Physical Security
Mobile devices, such as tablets, mobile phones, and smartphones, must be properly stored and secured in a cabinet or safe when not in use.
Utilize VPN
Enforce the use of virtual private network (VPN) connections with a strong protocol like IPSec between the mobile device and enterprise servers, especially if connecting to an insecure open wireless network.
Encrypt your device
Data should be encrypted on the device so that if it does fall into the wrong hands, it cannot be accessed in a usable form without the correct passwords.
Disable Unused Features
Every feature has the potential to be another point of vulnerability in a mobile system, so it’s good practice to disable any features that don’t serve a purpose in your organization.
Install an Antivirus Application
A mobile antivirus solution will protect devices against malicious code (such as xCodeGhost and iBackDoor) embedded in apps. Here is a quick list of the most popular mobile antivirus application:
- Kaspersky lab (AppStore, Google Play).
- McAfee (AppStore, Google Play).
- ESET (Google Play).
- AVAST (AppStore, Google Play).
Disable Wi-Fi and Bluetooth When Not Needed
Disable Wi-Fi and the discovery setting on Bluetooth connections to prevent bluejacking and bluesnarfing attacks and avoid connecting to an insecure open wireless network.
Software Updates
Keep the mobile operating system and its apps up to date. Everything from the mobile operating system to the games and miscellaneous apps are potential gateways for hackers to compromise the mobile device. Updating mobile devices and apps on a regular basis ensures the best protection against most mobile security threats.
Other mobile device security tips
Perform Regular Mobile Device Security Audits
At least once a year, conducting mobile security audit helps companies keep their compliance programs up to date, effective and aimed in the right direction.
Perform User Education
Implement a continuous information security awareness and training program that teaches employees about mobile device threats and enterprise mobile device management and security policies.
The Bottom Line in mobile device security
Mobile device security should be a primary concern. It isn’t simple to accomplish, and new attacks occur every day through new vulnerabilities. You need to always be aware of and notice anything unusual that happens on your device.
We hope that the tips mentioned in these article will help to enhance your mobile device security. If you like this article please subscribe to our newsletter and share with your friends.
Also check out how can you raise awareness among employees enhanced mobile devices usage and various other information security domain here.