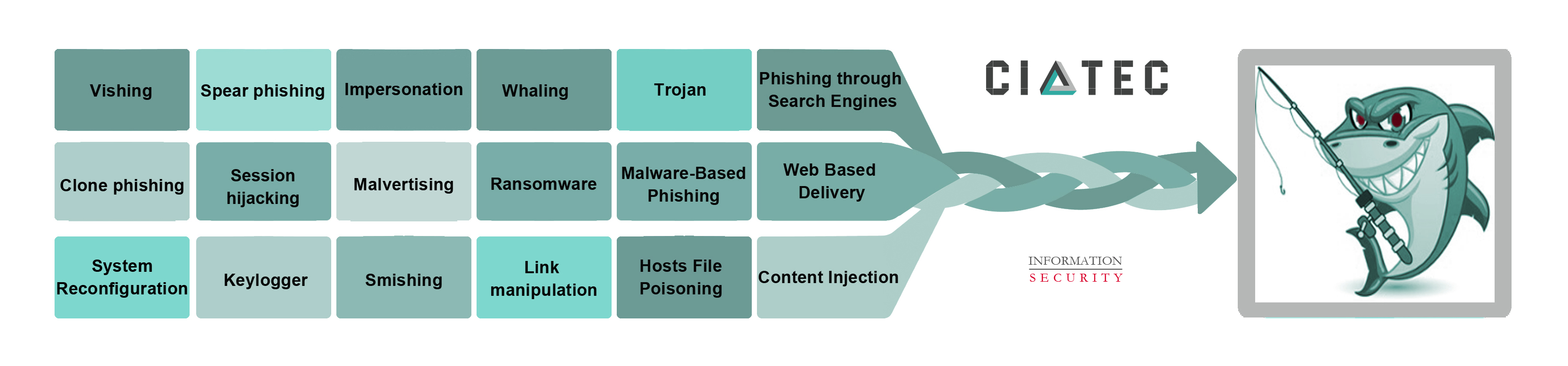
Using the guide below, organizations will be able to more quickly spot some of the most common types of phishing techniques and attacks that phishers use to trap a victim to own his credentials, bank accounts, social networking accounts or emails etc.
With that in mind, it’s imperative that organizations conduct security awareness training on an ongoing basis so that their employees and executives stay on top of emerging phishing attacks (For more information, read How to Identify a Phishing or Spoofing Email).
Spear phishing
A unique form of phishing in which the message is made to look as if it came from someone you know and trust as opposed to an informal third party.
Spear phishing works better than phishing because it uses information that it can find about you from email databases, friends’ lists, and the like.
Whaling
It is nothing more than phishing or spear phishing but for big users. Instead of sending out a To Whom It May Concern message to thousands of users, the whaler identifies one person from whom they can gain all the data they want—usually a manager or owner—and targets the phishing campaign at them.
Vishing
When you combine phishing with Voice over IP (VoIP), it becomes known as vishing, an elevated form of social engineering. Although crank calls have been in existence since the invention of the telephone, the rise in VoIP now makes it possible for someone to call you from almost anywhere in the world, without worrying about tracing, caller ID, and other land line–related features. They then pretend to be someone they are not in order to get data from you.
Session hijacking
In session hijacking, the phisher exploits the web session control mechanism to steal information from the user. Phishers place themselves between the user and host, thereby letting them monitor user traffic and launch specific attacks.
Keylogger
Another way of extracting information from a victim’s system is to use a piece of technology known as keylogger. Software in this category is designed to capture and report activity in the form of keyboard usage on a target system. When placed on a system, it gives the phisher the ability to monitor all activity on a system and reports back to the phisher.
Malvertising
Malvertising, or malicious advertising, is the use of online, malicious advertisements to spread malware and compromise systems. Generally this occurs through the injection of unwanted or malicious code into ads.
Smishing
A form of phishing, smishing is when the phisher tries to trick you into giving them your private information via a text or SMS message. Smishing is becoming an emerging and growing threat in the world of online security.
Content Injection
The content-injection social network phishing refers to inserting malicious content in social networks. The malicious content can often be in the form of bogus posts (e.g., tweets, posts in the Facebook feed or in LinkedIn feed) published by users whose accounts were affected with rogue apps. When the victim clicks on the link, he/she will be requested to provide his/her personal data, which may be used by the phisher for committing identity theft and other scams.
Link manipulation
Link manipulation is the technique in which the phisher sends a link to a malicious website. When the user clicks on the deceptive link, it opens up the phisher’s website instead of the website mentioned in the link.
Phishing through Search Engines
Search engine phishing occurs through online website search engines. Here, the person may encounter offers or messages that entice the person to visit the website. The search process may be legitimate, but the website is actually fake and only exists to steal the person’s personal information.
Web Based Delivery
Also known as “Man-in-the-middle “. Which is based on the principle that a system can be placed between two legitimate users to capture or exploit the information being sent between them. Both sides of the conversation assume that the man in the middle is the other end and communicate normally. This creates a security breach and allows the phisher to trace details during a transaction between the legitimate website and the user.
Malware-Based Phishing
Refers to scams that involve running malicious software on users’ PCs. Malware can be introduced as an email attachment, as a downloadable file from a web site, or by exploiting known security vulnerabilities
System Reconfiguration Attacks
Modify settings on a user’s PC for malicious purposes. For example: URLs in a favorites file might be modified to direct users to look alike websites where their information can be stolen..
Hosts File Poisoning
Hosts file poisoning involves injecting new entries for Internet sites into a computer’s hosts file, so that web site requests are either rerouted to another site, taking the user unwittingly to a fake “look alike” website where their information can be stolen.
Impersonation
Impersonation involves any act of pretending to be someone you are not. Impersonation can be done over the phone, by email, and so forth.
Trojan
A Trojan horse may be included as an attachment, try to log into your user account to collect credentials through the local machine. The acquired information is then transmitted to phishers.
Ransomware
Phishing ransomware attacks begin with what seems to look like a legitimate email, asking the recipient to open a file or click on a link. Once the attachment or link has been opened, the phisher then gains access to the device’s data and can distribute the malicious payload, asking the recipient end to pay a ransom in exchange for the return of stolen data or personal information.